6 Proven Ways For Businesses To Combat Cloud Security Risks
Cloud security is a set of policies, controls, practices and technologies that should work together to protect your cloud applications and systems. A list of 6 tips Every business we know has a lot of very sensitive data in the cloud, and now that most of us have moved to a remote work model, more data is stored in the cloud than ever before applications.
6 combat cloud security risks
-
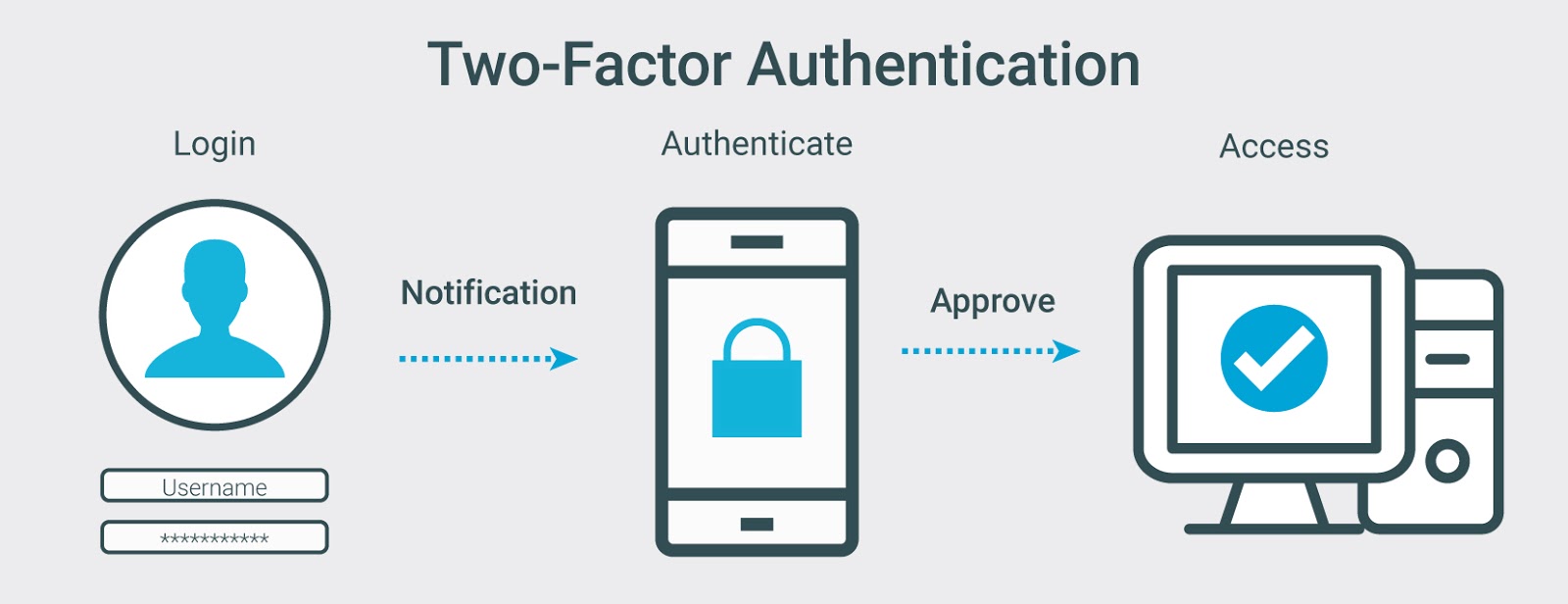
Set-up multi-factor authentication
Stolen credentials make it easier for hackers to access your business data and applications by stealing your credentials. A combination of complex usernames and passwords alone is not enough to secure your user accounts from hackers. Protect your cloud users with two-factor or multi-factor authentication to ensure that only authorized people can access your cloud applications and access sensitive information.
-
Assign access controls
Not all of your employees need to have access to every file, application, or data. By setting the right permission levels, each employee can view or access only the applications or data needed to complete their work. Assigning access controls ensures that your employees don’t accidentally modify any information they don’t have access to.
-
Leverage automation to monitor, log and analyze user activities
Real-time tracking and analysis of user activity can help you identify any anomalies or abnormal movements that are not part of your normal usage patterns. Such discrepancies can indicate a breach in your system, so it is essential to identify them early to prevent hackers from hacking your system and help you fix any security issues before they wreak havoc with your security system.
-
Provide anti-phishing training to your employees
Hackers can easily steal employee credentials to gain access to secure information through phishing. In this type of social engineering attack, the attacker sends fraudulent emails, texts, or websites to trick the victim into sharing access to sensitive information.

-
Create a comprehensive off-boarding process for departing employees
Ensure that your departing employees no longer have access to your cloud storage, data, systems, customer data and intellectual property. Since each employee will likely have access to different cloud applications and platforms, you need to set up a process to ensure that all access rights are removed for departing employees.
-
Cloud-to-cloud backup solutions
There is no doubt that there are legitimate risks associated with any cloud-based application or platform. However, the likelihood of losing data due to cloud provider error is low compared to human error. Say an employee accidentally deletes your data and a hacker gets the account password and corrupts the information, or an employee deletes their inbox and folders.

Conclusion
Cloud risk management requires customers to fully consider their exposure to threats and vulnerabilities, not just during. Public procurement, but also as an ongoing process. Clouds can provide a number of security benefits over traditional on-premises technology, such as the ability to thoroughly automate security-related processes, including threats and incidents Response.